Set a Sentinel environment and start collecting Windows logs on Azure

Hi Medium! Here we are again with a new article.
In this article, we will go through how we can set a basic environment to retrieve information from a target system and review its log on the Sentinel Azure platform.
Summary
- Windows 10 VM creation and Sysmon deployment
- Sentinel Creation
- Sysmon Installation on Windows
- Retrieve logs
- Conclusion
Windows 10 VM creation and Sysmon deployment
Creation of Win 10 on Azure
The first thing to do is to create a virtual machine on Azure, we go to “All resources” and look for “Microsoft Windows 10”

We create our machine, keep everything simple and to standard, and don’t add another functionality that may cost you extra fees, with this VM we will go with the cost of 4GB of RAM:

After creating the machine and setting the user and password we allow only our IP to connect to the machine via RDP

Once the security rule is updated, we connect to the machine via RDP

We connect now via RDP or we can simply download the RDP file.
Enter the password and click on ‘Yes’ to proceed:


Voila! Now we are connected.

Sentinel Creation
We need to create our workspace, so we search for Microsoft Sentinel in the search bar:

Once we are redirected to Sentinel, we create a new workspace:

We created a new Microsoft sentinel Workspace called light-monitoring:

We can mention that we have no logs

At this point, we need to link our Windows 10 machine to our sentinel.
To connect our Win 10 machine, we go to ‘Overview’ and click on ‘Azure Virtual Machine (VMs)’:
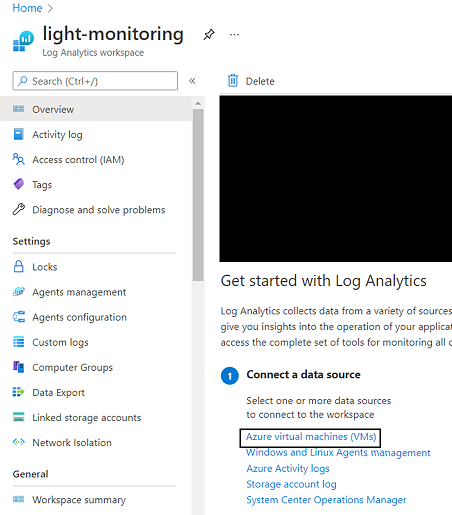
We look for our victim machine and we click on “connect”, we are so lucky that our machine is on Azure so the process is much easier, else we need to go to “Agent Management” under settings, and download the MMA Wizard or link the machine to sentinel via PowerShell.

We also installed our connector, via the data connector panel on Sentinel we added the “Windows security events via AMA” connector.
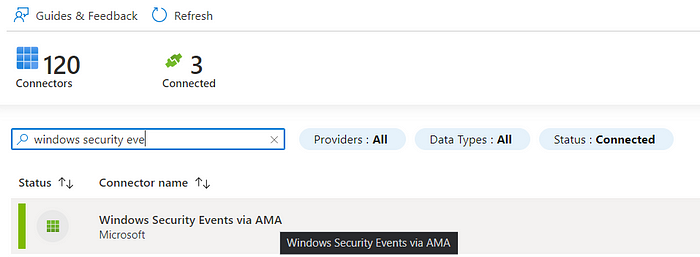
It will take some time; in the meantime, we go to our machine and install Sysmon.
Sysmon installation on Windows 10
To install Sysmon we will follow the steps:
1- Download Sysmon from here: Download Sysmon
2- Run the following command as Administrator:
.\Sysmon64.exe -accepteula -i sysmonconfig-export.xml
You can use .xml as a configuration file on this link: https://github.com/ion-storm/sysmon-config

To update the existing configuration we run the following command:
.\Sysmon64.exe -c sysmonconfig-export.xml

Events now can be viewed with “Event Viewer”. Go to “Applications and Services Logs” -> “Microsoft” -> “Windows” -> “Sysmon”

Installed and works perfectly
Retrieve logs
In Azure Agent management under settings, we can mention that we have one Windows machine connected which is ours, we go and click on “Go to logs”:

And here we are redirected to log management windows, that use KQL as a language to retrieve and filter logs, for more information about KQL check this link: https://docs.microsoft.com/en-us/sharepoint/dev/general-development/keyword-query-language-kql-syntax-reference
From here we can mention that our machine is well connected and we can retrieve the Heartbeat of our machine.

To retrieve Sysmon logs, first, we need to select the logs that we would like to see in “Agent Configuration” under settings as follows:

Adding those event logs, we are able now to retrieve system logs, and Sysmon logs:
- Microsoft-Windows-Sysmon
- Sys
We can retrieve specific logs under Sysmon like only Operational as follows in the next example:
- Microsoft-Windows-Sysmon/Operational

From this step, we can go back to Logs and run a command that retrieves all the Sysmon logs:

Conclusion
In this article, we learned how we can set Sentinel and collect logs from one of our machines on Azure, you can check this article on how to install Sysmon on Windows and how to create a parser on Sentinel using KQL.
In the next articles, we will talk more about more features on Sentinel, stay connected ;)
Hey, I hope that you enjoyed my article, if you have something to add or to correct please don’t hesitate to write a comment, see you soon ^^!
